Bounce attacks are a very tricky type of DDoS attacks. However, we can learn a lot from it when we take a deep dive into its technical make up and can better understand the logic and features of a bounce attack. This article aims to offer a bit more insight into bounce attacks and how to protect against them.
Bounce Attacks – A Background
For those who don’t know much about bounce attacks, let’s take a little time to get to grips with them. Bounce attacks are a DDoS attack with use the ‘leverage effect’ to cause greater damages. This means a hacker can create a heavy traffic attack with just a small number of requests. To put that into perspective, a hacker carrying out a bounce attack uses only around 1 GB of requests to create a bounce attack of up to 10 GB in traffic. Through concealment, the source IP address of a bounce attack is hidden owing to the mechanism of the attack. From a recipient's perspective, the source IP address of the attack shows as the IP address of a reflector.
Early on, attackers initiating bounce attacks such as SYN bounce attacks, change the source IP addresses of SYN packets to the IP addresses of the recipients and send the packets to many servers (which are the reflectors). The servers return SYN/ACK messages to the recipients according to the three-way handshake rules. In this case, a large number of unexpected SYN/ACK messages are sent from various IP addresses to the victims, creating SYN/ACK-based DDoS attacks. This is rarely used nowadays because it causes a high cost to the hackers and many servers have been protected against such attacks. However, the logic of this type of attack has a profound influence. Hackers have been exploring a great variety of reflectors and increasingly amplifying the effect on them.
What are ‘Reflectors’?
The criteria regarding reflectors are as follows:
1. Reflectors must be widely distributed and large in quantity.
2. There must be a function, vulnerability, module, or interaction mechanism that enables "bounce".
It is noticeable that in recent years, the DNS servers, NTP servers, and SSDP devices widely deployed across the internet have been used intentionally by hackers as reflectors. The DDoS attacks initiated with these reflectors have emerged account for a large proportion of DDoS attacks over the past few years. Although these reflectors work on L7, they mainly leverage heavy traffic to cause network congestion, which is basically similar to attacks with large UDP packets.
Therefore, you can protect against such attacks simply by using ACL to disable the ports of reflectors (such as the UDP 1900 ports of SSDP devices and UDP 123 ports of NTP servers), or by filtering out the typical fields for initiating the attacks (such as uuid for initiating attacks with SSDP servers).
Bounce Attacks on WordPress
Now that we’ve covered the logic and background behind Bounce Attacks, lets take a look at on WordPress specific Bounce Attacks. Unlike the other bounce attacks such as NTP bounce attacks, a WordPress bounce attack is carried out on layer 7, making it a type of CC attack. WordPress bounce attacks have been reported from as early as 2014. According to the results of detection of DDoS attacks on Alibaba Cloud Security users, WordPress bounce attacks still account for a large proportion of CC attacks and generally are able to exhaust the processing capacity of a common site with a low cost and light traffic (compared with traffic-dependent bounce attacks).
Bounce Attacks on WordPress: Unique Traits
Considering that a WordPress bounce attack has unique traits, let’s quickly go over its unique characteristics.
WordPress, as I’m sure you all know, is a popular blog platform on which about 20% of all the websites around the world are built on. WordPress bounce attacks use millions of these websites from across the internet which satisfy reflectors criterion 1 (as mentioned previously), and the pingback mechanism provided by a module named XML- RPC which satisfies criterion 2 (also mentioned above).
The pingback mechanism originally serves as a means to notify a website system of article referencing. At a simple POST request, the mechanism sends a reference link and reference page content to a referenced site or blog. Upon receiving a pingback request, WordPress automatically returns a response to the source page to verify the reference link. Using this mechanism, attackers can specify target addresses and construct pingback requests containing valid links to achieve the bounce effect for CC attacks. Such a request can be constructed simply with the curl command. Therefore, it is quite easy for an attacker in possession of a certain number of WordPress websites to carry out the attack on multiple targets.
Here is a screenshot of a WordPress bounce attack on a website detected by Anti-DDoS Pro.

The above figure indicates that the pingback request was sent from an IP address in Chile. At present, there are millions of such requests from around the world, and many of them are sent from South America, North America, and the Chinese Mainland.
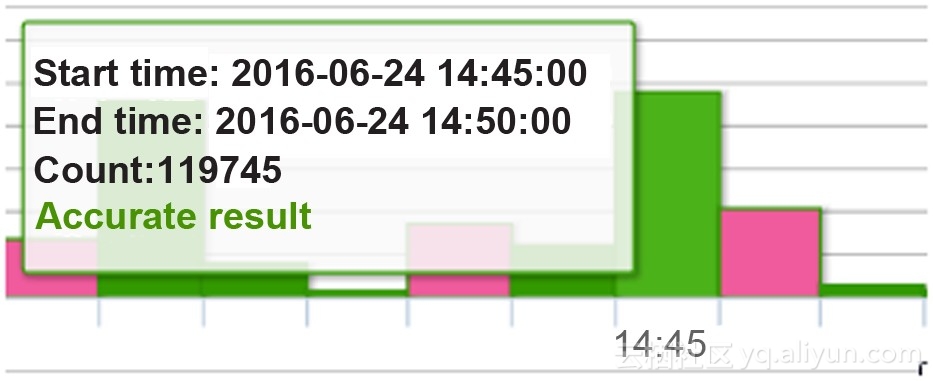
The following protection log of Anti-DDoS Pro shows that about 120,000 such requests were detected within 5 minutes. This example from Alibaba Cloud Security allows you to understand the larger picture of CC attacks on users in a day.
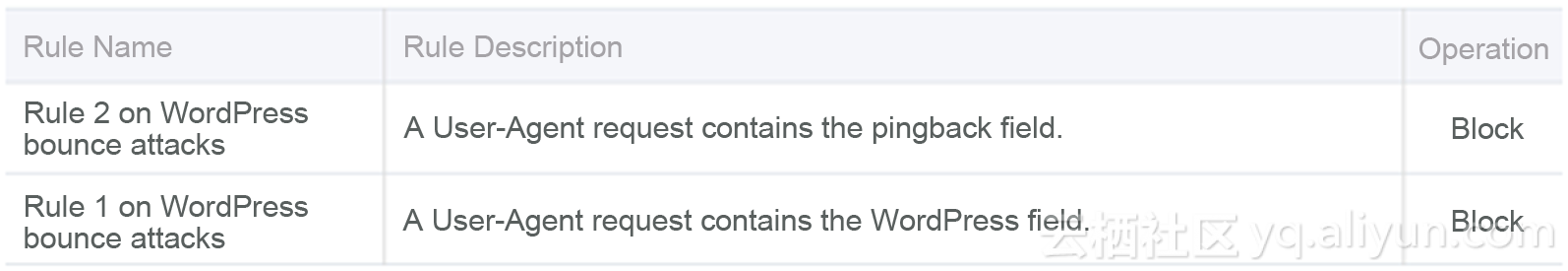
According to the preceding introduction, when a WordPress bounce attack is carried out, the user-agent request must include the WordPress or pingback field, while the source IP address may be variable. These characteristics allow us to protect against the attacks simply by rejecting the requests that contain the fields (similarly, ACL is used to protect again NTP bounce attacks by disabling UDP port 123.)
How to Detect and Prevent WordPress Bounce Attacks:
1.Take Nginx as an example. When it is suspected that a website is under CC attack (challenge collapse attack), you can tail log files to check whether a large number of requests containing the pingback field have been generated. Alternatively, you can use the following command to collect the statistics:
![]()
2. When such attacks are detected, open the Nginx configuration file of the website (/etc/nginx/nginx.conf or /etc/nginx/sites-enabled/your-site depending on the specific Nginx and Linux versions), locate the server definition, and add the following if statement (case-sensitive) to somewhere in the server definition:

3.The preceding statement returns the error 403 (access denied) message when detecting the WordPress or pingback field in a user-agent request. After modifying the Nginx configuration, reload it using the following command:
![]()
4. After configuration is complete, you can run the curl or wget command with the specified user-agent request to check whether error 403 messages are received. If yes, the configuration is correct.
Conclusion
With the above configuration, the server can now block such attacks. Configuring local servers to achieve protection is not applicable to users without O&M knowledge or large-scale CC attacks.
In these cases, it’s recommended to turn to high-performance cloud mitigation services to block these attacks. Currently, the Anti-DDoS Suite from Alibaba Cloud Security supports customized policies for addressing such attacks. In addition, Web Application Firewall (WAF) offers customized rules to enable users to complete simple configuration for protection.