从新浪移动过来了
关于SMB版本的扫描
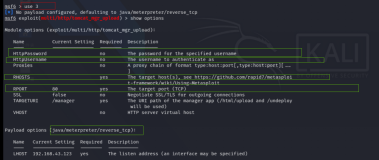
那个smb2的溢出,其实在metasploit里面有两个扫描器可以用,效果都差不多,只是一个判断的更加详细,一个只是粗略的判断。
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
|
Welcome to the Metasploit Web Console!
_ _
_ | | (_)_
____ ____| |_ ____ ___ ____ | | ___ _| |_
| \ / _ ) _)/ _ |/___) _ \| |/ _ \| | _)
| | | ( (/ /| |_( ( | |___ | | | | | |_| | | |__
|_|_|_|\____)\___)_||_(___/| ||_/|_|\___/|_|\___)
|_|
=[ metasploit v3.4.2-dev [core:3.4 api:1.0]
+ -- --=[ 566 exploits - 283 auxiliary
+ -- --=[ 210 payloads - 27 encoders - 8 nops
=[ svn r9834 updated 329 days ago (2010.07.14)
Warning: This copy of the Metasploit Framework was last updated 329 days ago.
We recommend that you update the framework at least every other day.
For information on updating your copy of Metasploit, please see:
http://www.metasploit.com/redmine/projects/framework/wiki/Updating
>> search smb
[*] Searching loaded modules for pattern 'smb'...
Auxiliary
=========
Name Rank Description
---- ---- -----------
admin/oracle/ora_ntlm_stealer normal Oracle SMB Relay Code Execution
admin/smb/samba_symlink_traversal normal Samba Symlink Directory Traversal
dos/windows/smb/ms05_047_pnp normal Microsoft Plug and Play Service Registry Overflow
dos/windows/smb/ms06_035_mailslot normal Microsoft SRV.SYS Mailslot Write Corruption
dos/windows/smb/ms06_063_trans normal Microsoft SRV.SYS Pipe Transaction No Null
dos/windows/smb/ms09_001_write normal Microsoft SRV.SYS WriteAndX Invalid DataOffset
dos/windows/smb/ms09_050_smb2_negotiate_pidhigh normal Microsoft SRV2.SYS SMB Negotiate ProcessID Function Table Dereference
dos/windows/smb/ms09_050_smb2_session_logoff normal Microsoft SRV2.SYS SMB2 Logoff Remote Kernel NULL Pointer Dereference
dos/windows/smb/ms10_006_negotiate_response_loop normal Microsoft Windows 7 / Server 2008 R2 SMB Client Infinite Loop
dos/windows/smb/rras_vls_null_deref normal Microsoft RRAS InterfaceAdjustVLSPointers NULL Dereference
dos/windows/smb/vista_negotiate_stop normal Microsoft Vista SP0 SMB Negotiate Protocol DoS
fuzzers/smb/smb2_negotiate_corrupt normal SMB Negotiate SMB2 Dialect Corruption
fuzzers/smb/smb_create_pipe normal SMB Create Pipe Request Fuzzer
fuzzers/smb/smb_create_pipe_corrupt normal SMB Create Pipe Request Corruption
fuzzers/smb/smb_negotiate_corrupt normal SMB Negotiate Dialect Corruption
fuzzers/smb/smb_ntlm1_login_corrupt normal SMB NTLMv1 Login Request Corruption
fuzzers/smb/smb_tree_connect normal SMB Tree Connect Request Fuzzer
fuzzers/smb/smb_tree_connect_corrupt normal SMB Tree Connect Request Corruption
scanner/smb/pipe_auditor normal SMB Session Pipe Auditor
scanner/smb/pipe_dcerpc_auditor normal SMB Session Pipe DCERPC Auditor
scanner/smb/smb2 normal SMB 2.0 Protocol Detection
scanner/smb/smb_enumshares normal SMB Share Enumeration
scanner/smb/smb_enumusers normal SMB User Enumeration (SAM EnumUsers)
scanner/smb/smb_login normal SMB Login Check Scanner
scanner/smb/smb_lookupsid normal SMB Local User Enumeration (LookupSid)
scanner/smb/smb_version normal SMB Version Detection
server/capture/smb normal Authentication Capture: SMB
Exploits
========
Name Rank Description
---- ---- -----------
netware/smb/lsass_cifs average Novell NetWare LSASS CIFS.NLM Driver Stack Buffer Overflow
windows/browser/java_ws_arginject_altjvm excellent Sun Java Web Start Plugin Command Line Argument Injection
windows/browser/ms10_022_ie_vbscript_winhlp32 great Internet Explorer Winhlp32.exe MsgBox Code Execution
windows/fileformat/ursoft_w32dasm good URSoft W32Dasm Disassembler Function Buffer Overflow
windows/fileformat/vlc_smb_uri great VideoLAN Client (VLC) Win32 smb:// URI Buffer Overflow
windows/smb/ms03_049_netapi good Microsoft Workstation Service NetAddAlternateComputerName Overflow
windows/smb/ms04_007_killbill low Microsoft ASN.1 Library Bitstring Heap Overflow
windows/smb/ms04_011_lsass good Microsoft LSASS Service DsRolerUpgradeDownlevelServer Overflow
windows/smb/ms04_031_netdde good Microsoft NetDDE Service Overflow
windows/smb/ms05_039_pnp good Microsoft Plug and Play Service Overflow
windows/smb/ms06_025_rasmans_reg good Microsoft RRAS Service RASMAN Registry Overflow
windows/smb/ms06_025_rras average Microsoft RRAS Service Overflow
windows/smb/ms06_040_netapi great Microsoft Server Service NetpwPathCanonicalize Overflow
windows/smb/ms06_066_nwapi good Microsoft Services MS06-066 nwapi32.dll
windows/smb/ms06_066_nwwks good Microsoft Services MS06-066 nwwks.dll
windows/smb/ms06_070_wkssvc normal Microsoft Workstation Service NetpManageIPCConnect Overflow
windows/smb/ms08_067_netapi great Microsoft Server Service Relative Path Stack Corruption
windows/smb/ms09_050_smb2_negotiate_func_index good Microsoft SRV2.SYS SMB Negotiate ProcessID Function Table Dereference
windows/smb/msdns_zonename great Microsoft DNS RPC Service extractQuotedChar() Overflow (SMB)
windows/smb/netidentity_xtierrpcpipe great Novell NetIdentity Agent XTIERRPCPIPE Named Pipe Buffer Overflow.
windows/smb/psexec excellent Microsoft Windows Authenticated User Code Execution
windows/smb/smb_relay excellent Microsoft Windows SMB Relay Code Execution
windows/smb/timbuktu_plughntcommand_bof great Timbuktu <= 8.6.6 PlughNTCommand Named Pipe Buffer Overflow
>> use auxiliary/scanner/smb/smb2
>> info
Name: SMB 2.0 Protocol Detection
Version: 9550
License: Metasploit Framework License (BSD)
Rank: Normal
Provided by:
hdm <
hdm
@metasploit.com>
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
RPORT 445 yes The target port
THREADS 1 yes The number of concurrent threads
Description:
Detect systems that support the SMB 2.0 protocol
>> set RHOSTS 172.16.1.0/24
RHOSTS => 172.16.1.0/24
>> set THREADS 100
THREADS => 100
>> info
Name: SMB 2.0 Protocol Detection
Version: 9550
License: Metasploit Framework License (BSD)
Rank: Normal
Provided by:
hdm <
hdm
@metasploit.com>
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 172.16.1.0/24 yes The target address range or CIDR identifier
RPORT 445 yes The target port
THREADS 100 yes The number of concurrent threads
Description:
Detect systems that support the SMB 2.0 protocol
>> run
[*] 172.16.1.102 supports SMB 2 [dialect 255.2] and has been online for 23 hours
[*] 172.16.1.107 supports SMB 2 [dialect 255.2] and has been online for 2 hours
[*] 172.16.1.110 supports SMB 2 [dialect 255.2] and has been online for 6 hours
[*] Scanned 042 of 256 hosts (016% complete)
[*] Scanned 055 of 256 hosts (021% complete)
[*] Scanned 084 of 256 hosts (032% complete)
[*] Scanned 104 of 256 hosts (040% complete)
[*] Scanned 128 of 256 hosts (050% complete)
[*] Scanned 155 of 256 hosts (060% complete)
[*] Scanned 184 of 256 hosts (071% complete)
[*] Scanned 205 of 256 hosts (080% complete)
[*] Scanned 235 of 256 hosts (091% complete)
[*] Scanned 256 of 256 hosts (100% complete)
[*] Auxiliary module execution completed
>> back
>> use auxiliary/scanner/smb/smb_version
>> info
Name: SMB Version Detection
Version: 9827
License: Metasploit Framework License (BSD)
Rank: Normal
Provided by:
hdm <
hdm
@metasploit.com>
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
THREADS 1 yes The number of concurrent threads
Description:
Display version information about each system
>> set RHOSTS 172.16.1.0/24
RHOSTS => 172.16.1.0/24
>> set THREADS 100
THREADS => 100
>> info
Name: SMB Version Detection
Version: 9827
License: Metasploit Framework License (BSD)
Rank: Normal
Provided by:
hdm <
hdm
@metasploit.com>
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 172.16.1.0/24 yes The target address range or CIDR identifier
THREADS 100 yes The number of concurrent threads
Description:
Display version information about each system
>> run
[*] Scanned 026 of 256 hosts (010% complete)
[*] Scanned 061 of 256 hosts (023% complete)
[*] Scanned 087 of 256 hosts (033% complete)
[*] 172.16.1.107 is running Windows 7 Ultimate (Build 7600) (language: Unknown) (name:PC) (domain:WORKGROUP)
[*] 172.16.1.110 is running Windows 7 Ultimate (Build 7600) (language: Unknown) (name:YANG*-PC) (domain:WORKGROUP)
[*] 172.16.1.102 is running Windows 7 Ultimate (Build 7600) (language: Unknown) (name:WANG*) (domain:YANGYANGWO)
[*] 172.16.1.111 is running Windows XP Service Pack 3 (language: Chinese - Traditional) (name:WWW-95A235B5556) (domain:WORKGROUP)
[*] Scanned 112 of 256 hosts (043% complete)
[*] Scanned 133 of 256 hosts (051% complete)
[*] Scanned 168 of 256 hosts (065% complete)
[*] Scanned 181 of 256 hosts (070% complete)
[*] Scanned 208 of 256 hosts (081% complete)
[*] Scanned 232 of 256 hosts (090% complete)
[*] Scanned 256 of 256 hosts (100% complete)
[*] Auxiliary module execution completed
|
本文转自文东会博客51CTO博客,原文链接http://blog.51cto.com/hackerwang/1247880如需转载请自行联系原作者
谢文东666