The Complete List
- Persistent Cookies and DNS Rebinding Redux
- iPhone SSL Warning and Safari Phishing
- RFC 1918 Blues
- Slowloris HTTP DoS
- CSRF And Ignoring Basic/Digest Auth
- Hash Information Disclosure Via Collisions - The Hard Way
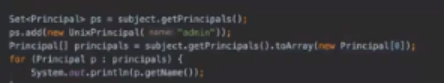
- Socket Capable Browser Plugins Result In Transparent Proxy Abuse
- XMLHTTPReqest “Ping” Sweeping in Firefox 3.5+
- Session Fixation Via DNS Rebinding
- Quicky Firefox DoS
- DNS Rebinding for Credential Brute Force
- SMBEnum
- DNS Rebinding for Scraping and Spamming
- SMB Decloaking
- De-cloaking in IE7.0 Via Windows Variables
- itms Decloaking
- Flash Origin Policy Issues
- Cross-subdomain Cookie Attacks
- HTTP Parameter Pollution (HPP)
- How to use Google Analytics to DoS a client from some website.
- Our Favorite XSS Filters and how to Attack them
- Location based XSS attacks
- PHPIDS bypass
- I know what your friends did last summer
- Detecting IE in 12 bytes
- Detecting browsers javascript hacks
- Inline UTF-7 E4X javascript hijacking
- HTML5 XSS
- Opera XSS vectors
- New PHPIDS vector
- Bypassing CSP for fun, no profit
- Twitter misidentifying context
- Ping pong obfuscation
- HTML5 new XSS vectors
- About CSS Attacks
- Web pages Detecting Virtualized Browsers and other tricks
- Results, Unicode Left/Right Pointing Double Angel Quotation Mark
- Detecting Private Browsing Mode
- Cross-domain search timing
- Bonus Safari XXE (only affecting Safari 4 Beta)
- Apple's Safari 4 also fixes cross-domain XML theft
- Apple's Safari 4 fixes local file theft attack
- A more plausible E4X attack
- A brief description of how to become a CA
- Creating a rogue CA certificate
- Browser scheme/slash quirks
- Cross-protocol XSS with non-standard service ports
- Forget sidejacking, clickjacking, and carjacking: enter “Formjacking”