#!/usr/bin/python
# Simple Log File Analyzer by Valentin Hoebel
# Version 1.0 (6th June 2010)
# Contact me at valentin@xenuser.org
# Website: I am sure you will find me! :)
# ASCII FOR BREAKFAST
# Description:
# This tool helps you to find hack attempts
# within webserver log files (e.g. Apache2 access logs).
# Features:
# - Error handling
# - Scan a log file for four different attack types
# - Display a short scan report
# - Write scan results to a new log file
# - Easy to use (everything is simple and automated
# Usage example:
# scan_log.py -file vhost_access.log
# Known issue:
# XSS attempt discovery feature can be a little bit buggy.
# Tested with:
# Apache2 log files only. Sry guys! But I am sure
# that every other webserver log file will work aswell.
# Disclaimer:
# I am not responsible if this script or you cause any damage
# to your system. The memory consumption can become
# quite large and the generated reports very huge. So be sure
# you know what you are doing. I highly recommend you
# download your log files on a separate machine and
# analyze these files there.
# I know that there are much better tools, but well, I do
# this for learning and fun =)
# Attention: Tool is far away from being perfect, so don't rely a 100 percent on it.
# A BIG "Thank you!" to all who publish their awesome Python
# scripts online and help other ppl learning this language.
# Modify, distribute, share and copy this code in any way you like!
# Power to the cows!
import sys, string, re, time
from time import strftime, localtime
def print_usage():
print ""
print ""
print "________________________________________________"
print "Simple Log File Analyzer"
print "by Valentin Hoebel (valentin@xenuser.org)"
print ""
print "Version 1.0 (6th June 2010) ^__^"
print " (oo)/________"
print " (__)/ )/// "
print " ||----w |"
print "Power to teh cows! || ||"
print "________________________________________________"
print ""
print "[!] Use parameter --help for help!"
print ""
print ""
return
def print_help():
print ""
print ""
print "________________________________________________"
print "Simple Log File Analyzer"
print "by Valentin Hoebel (valentin@xenuser.org)"
print ""
print "Version 1.0 (6th June 2010) ^__^"
print " (oo)/________"
print " (__)/ )/// "
print " ||----w |"
print "Power to teh cows! || ||"
print "________________________________________________"
print ""
print "The Simple Log File Analyzer helps you to find"
print "common hack attempts within your webserver log."
print ""
print "Supported attacks:"
print " - SQL Injection"
print " - Local File Inclusion"
print " - Remote File Inclusion"
print " - Cross-Site Scripting"
print ""
print "This scanner doesn't find everything so don't"
print "rely on it!"
print ""
print "Usage example:"
print "scan_log.py -file vhost_access.log"
print ""
print "Options:"
print " -file <file> (starts the main analyzing function"
print " --help (displays this text)"
print ""
print "Features:"
print " - Error handling"
print " - Scan a log file for four different attack types"
print " - Display a short scan report"
print " - Write scan results to a new log file"
print " - Easy to use (everything is simple and automated)"
print ""
print "Additional information:"
print "I only tested this tool with Apache2 log files (up to 2000 lines)."
print "It may happen that the tool crashes when the provided log"
print "file is too big or contains too many lines/characters."
print "Scanning a 4000 lines log file only takes one second."
print ""
print "Hint: The XSS discovery feature is a little bit buggy."
print ""
print ""
return
def print_banner():
print ""
print ""
print "________________________________________________"
print "Simple Log File Analyzer"
print "by Valentin Hoebel (valentin@xenuser.org)"
print ""
print "Version 1.0 (6th June 2010) ^__^"
print " (oo)/________"
print " (__)/ )/// "
print " ||----w |"
print "Power to teh cows! || ||"
print "________________________________________________"
return
# Define the function for analyzing log files
def analyze_log_file(provided_file):
# Defining some important vars
sqli_found_list = {}
lfi_found_list = {}
rfi_found_list = {}
xss_found_list = {}
# I know, there are better methods for doing/defining this...
sql_injection_1 = "UNION"
sql_injection_2 = "ORDER"
sql_injection_3 = "GROUP"
local_file_inclusion_1 = "/etc/passwd"
local_file_inclusion_2 = "/etc/passwd%20"
local_file_inclusion_3 = "=../"
remote_file_inclusion_1 = "c99"
remote_file_inclusion_2 = "=http://"
cross_site_scripting_1 = "XSS"
cross_site_scripting_2 = "alert"
cross_site_scripting_3 = "String.fromCharCode"
cross_site_scripting_4 = "iframe"
cross_site_scripting_5 = "javascript"
print "[i] >>", provided_file
print "[i] Assuming you provided a readable log file."
print "[i] Trying to open the log file now."
print ""
# Opening the log file
try:
f = open(provided_file, "r")
except IOError:
print "[!] The file doesn't exist."
print "[!] Exiting now!"
print ""
sys.exit(1)
print "[i] Opening the log file was successfull."
print "[i] Moving on now..."
print ""
# Storing every single line in a list
line_list = [line for line in f]
max_lines = len(line_list)
print "[i] The file contains", max_lines, "lines."
print "[i] Now looking for possible hack attempts..."
# Viewing every single line
for x in xrange(1, max_lines):
current_line = line_list[x:x+1]
# For some strange list behaviour we convert the list into a string
current_line_string = "".join(current_line)
# Search for SQL injections
find_sql_injection_1 = re.findall(sql_injection_1, current_line_string)
if len(find_sql_injection_1) != 0:
sqli_found_list[x+1] = current_line_string
else:
find_sql_injection_2 = re.findall(sql_injection_2, current_line_string)
if len(find_sql_injection_2) != 0:
sqli_found_list[x+1] = current_line_string
else:
find_sql_injection_3 = re.findall(sql_injection_3, current_line_string)
if len(find_sql_injection_3) != 0:
sqli_found_list[x+1] = current_line_string
# Search for local file inclusions
find_local_file_inclusion_1 = re.findall(local_file_inclusion_1, current_line_string)
if len(find_local_file_inclusion_1) != 0:
lfi_found_list[x+1] = current_line_string
else:
find_local_file_inclusion_2 = re.findall(local_file_inclusion_2, current_line_string)
if len(find_local_file_inclusion_2) != 0:
lfi_found_list[x+1] = current_line_string
else:
find_local_file_inclusion_3 = re.findall(local_file_inclusion_3, current_line_string)
if len(find_local_file_inclusion_3) != 0:
lfi_found_list[x+1] = current_line_string
# Search for remote file inclusions
find_remote_file_inclusion_1 = re.findall(remote_file_inclusion_1, current_line_string)
if len(find_remote_file_inclusion_1) != 0:
rfi_found_list[x+1] = current_line_string
else:
find_remote_file_inclusion_2 = re.findall(remote_file_inclusion_2, current_line_string)
if len(find_remote_file_inclusion_2) != 0:
rfi_found_list[x+1] = current_line_string
# Search for cross-site scripting attempts
find_cross_site_scripting_1 = re.findall(cross_site_scripting_1, current_line_string)
if len(find_cross_site_scripting_1) != 0:
xss_found_list[x+1] = current_line_string
else:
find_cross_site_scripting_2 = re.findall(cross_site_scripting_2, current_line_string)
if len(find_cross_site_scripting_2) != 0:
xss_found_list[x+1] = current_line_string
else:
find_cross_site_scripting_3 = re.findall(cross_site_scripting_3, current_line_string)
if len(find_cross_site_scripting_3) != 0:
xss_found_list[x+1] = current_line_string
else:
find_cross_site_scripting_4= re.findall(cross_site_scripting_4, current_line_string)
if len(find_cross_site_scripting_4) != 0:
xss_found_list[x+1] = current_line_string
else:
find_cross_site_scripting_5 = re.findall(cross_site_scripting_5, current_line_string)
if len(find_cross_site_scripting_5) != 0:
xss_found_list[x+1] = current_line_string
# Close the file we opened recently
f.close()
# Generating a short report
print "[i] Done."
print ""
print "[#] Simple report for analyzed log file"
check_for_sqli_attempts = len(sqli_found_list)
if check_for_sqli_attempts > 0:
print "[!]", check_for_sqli_attempts, "SQL injection attempt(s) was/were found."
else:
print "[+] No SQL injection attempt was found."
check_for_lfi_attempts = len(lfi_found_list)
if check_for_lfi_attempts > 0:
print "[!]", check_for_lfi_attempts, "local file inclusion attempt(s) was/were found."
else:
print "[+] No local file inclusion attempt was found."
check_for_rfi_attempts = len(rfi_found_list)
if check_for_rfi_attempts > 0:
print "[!]", check_for_rfi_attempts, "remote file inclusion attempt(s) was/were found."
else:
print "[+] No remote file inclusion attempt was found."
check_for_xss_attempts = len(xss_found_list)
if check_for_xss_attempts > 0:
print "[!]", check_for_xss_attempts, "cross-site scripting attempt(s) was/were found."
else:
print "[+] No crosse-site scripting attempt was found."
# Now generate the report
print ""
print "[i] Generating report..."
# Define variables for the report name
time_string = strftime("%a_%d_%b_%Y_%H_%M_%S", localtime())
time_string_for_report = strftime("%a the %d %b %Y, %H:%M:%S", localtime())
name_of_report_file = provided_file + "_scan_report_from_" + time_string
# Convert the ints to strings
sqli_numbers = str(check_for_sqli_attempts)
lfi_numbers = str(check_for_lfi_attempts)
rfi_numbers = str(check_for_rfi_attempts)
xss_numbers = str(check_for_xss_attempts)
# Create the file
generated_report = open(name_of_report_file, "w")
# Write the content
generated_report.write("/n")
generated_report.write("Simple Log File Analyzer/n")
generated_report.write("by Valentin Hoebel (valentin@xenuser.org)/n")
generated_report.write("/n")
generated_report.write("Version 1.0 (6th June 2010) ^__^/n")
generated_report.write(" (oo)/________/n")
generated_report.write(" (__)/ )/// /n")
generated_report.write(" ||----w |/n")
generated_report.write("Power to teh cows! || ||/n")
generated_report.write("________________________________________________/n")
generated_report.write("/n")
generated_report.write("Scan report for " +provided_file + " on " + time_string_for_report + "/n")
generated_report.write("Hint: XSS attempt discovery feature might be a little bit buggy./n")
generated_report.write("/n")
generated_report.write("/n")
generated_report.write("Number of possible SQL injection attempts found: " + sqli_numbers + "/n")
generated_report.write("Number of possible local file inclusion attempts found: " + lfi_numbers + "/n")
generated_report.write("Number of possible remote file inclusion attempts found: " + rfi_numbers + "/n")
generated_report.write("Number of possible cross-site scripting attempts found: " + xss_numbers + "/n")
generated_report.write("/n")
generated_report.write("/n")
if len(sqli_found_list) != 0:
sqli_found_list_string = ""
sqli_found_list_string = "".join(str(sqli_found_list))
generated_report.write("Details for the SQL injection attempts (line, log entry)/n")
generated_report.write("------------------------------------------------/n")
generated_report.write(sqli_found_list_string)
generated_report.write("/n")
generated_report.write("/n")
generated_report.write("/n")
if len(lfi_found_list) != 0:
lfi_found_list_string = ""
lfi_found_list_string = "".join(str(lfi_found_list))
generated_report.write("Details for the local file inclusion attempts (line, log entry)/n")
generated_report.write("------------------------------------------------/n")
generated_report.write(lfi_found_list_string)
generated_report.write("/n")
generated_report.write("/n")
generated_report.write("/n")
if len(rfi_found_list) != 0:
rfi_found_list_string = ""
rfi_found_list_string = "".join(str(rfi_found_list))
generated_report.write("Details for the remote file inclusion attempts (line, log entry)/n")
generated_report.write("------------------------------------------------/n")
generated_report.write(rfi_found_list_string)
generated_report.write("/n")
generated_report.write("/n")
generated_report.write("/n")
if len(xss_found_list) != 0:
xss_found_list_string = ""
xss_found_list_string = "".join(str(xss_found_list))
generated_report.write("Details for the cross-site scripting attempts (line, log entry)/n")
generated_report.write("------------------------------------------------/n")
generated_report.write(xss_found_list_string)
generated_report.write("/n")
generated_report.write("/n")
generated_report.write("/n")
# Close the file
generated_report.close()
print "[i] Finished writing the report."
print "[i] Hint: The report file can become quite large."
print "[i] Hint: The XSS attempt discovery feature might be a little bit buggy."
print ""
print "[i] That's it, bye!"
print ""
print ""
return
# End of the log file function
# Checking if argument was provided
if len(sys.argv) <=1:
print_usage()
sys.exit(1)
for arg in sys.argv:
# Checking if help was called
if arg == "--help":
print_help()
sys.exit(1)
# Checking if a log file was provided, if yes -> go!
if arg == "-file":
provided_file = sys.argv[2]
print_banner()
# Start the main analyze function
analyze_log_file(provided_file)
sys.exit(1)
### EOF ###
Simple Log File Analyzer
2010-06-27
712
版权
版权声明:
本文内容由阿里云实名注册用户自发贡献,版权归原作者所有,阿里云开发者社区不拥有其著作权,亦不承担相应法律责任。具体规则请查看《
阿里云开发者社区用户服务协议》和
《阿里云开发者社区知识产权保护指引》。如果您发现本社区中有涉嫌抄袭的内容,填写
侵权投诉表单进行举报,一经查实,本社区将立刻删除涉嫌侵权内容。
简介:
#!/usr/bin/python
# Simple Log File Analyzer by Valentin Hoebel
# Version 1.
目录
相关文章
|
5月前
|
4月前
|
运维
应用服务中间件
网络安全
|
7月前
|
关系型数据库
MySQL
数据库
阿里云Mysql数据库物理全备文件恢复到自建数据库Mysql报错:InnoDB: Log file ./...xtrabacku
阿里云Mysql数据库物理全备文件恢复到自建数据库Mysql报错:InnoDB: Log file ./...xtrabacku
51
0
0
|
8月前
|
应用服务中间件
PHP
nginx
PHP ERROR: failed to open error_log (/usr/var/log/php-fpm.log): No such file or directory (2)
PHP ERROR: failed to open error_log (/usr/var/log/php-fpm.log): No such file or directory (2)
56
1
1
|
9月前
|
Java
成功解决:ERROR StatusLogger No log4j2 configuration file found.
成功解决:ERROR StatusLogger No log4j2 configuration file found.
232
0
0
|
12月前
|
Oracle
前端开发
关系型数据库
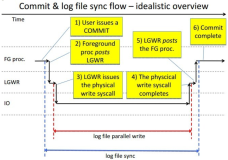
log file sync 和 log file parallel write等待事件的区别和联系
log file parallel write 和log file sync这两个等待事件关系密切,很多人对这两个等待事件有一些误解,我们先来看看Oracle官方文档的解释:
83
0
0
|
存储
缓存
数据处理
完全揭秘log file sync等待事件
什么是log file sync等待事件呢?在一个提交(commit)十分频繁的数据库中,一般会出现log file sync等待事件,当这个等待事件出现在top5中,这个时侯我们需要针对log file sync等待事件进行优化,一定要尽快分析并解决问题,否则当log file sync等待时间从几毫秒直接到20几毫秒可能导致系统性能急剧下降,甚至会导致短暂的挂起。
1287
0
0
|
Kubernetes
容器
logdna过滤log file
本文在使用logdna的基础上,将logdna-agent-master.yml文件直接部署到k8s cluster中. 通过设置yml文件或者在logdna UI界面上的过滤操作,达到了预期的效果。
2222
0
0
|
关系型数据库
Oracle
redo log file
1020
0
0
|
监控
调度
log file sync
735
0
0
热门文章
最新文章
1
更优性能与性价比,从自建 ELK 迁移到 SLS 开始
2
使用Java代码打印log日志
3
Linux手动清理Linux脚本日志定时清理日志和log文件执行表达式
4
/var/log/auth.log日志详解
5
工具变量法(两阶段最小二乘法2SLS)线性模型分析人均食品消费时间序列数据和回归诊断(下)
6
Linux&Windows 日志分析 陇剑杯 CTF
7
R语言计量经济学:工具变量法(两阶段最小二乘法2SLS)线性模型分析人均食品消费时间序列数据和回归诊断
8
提升日志管理效率:掌握CKA认证中的边车容器技巧
9
centos7 Nginx Log日志统计分析 常用命令
10
基于Java的公司员工工作日志办公系统的设计与实现(源码+lw+部署文档+讲解等)
1
在云效中,如果你看不到错误日志,可能是因为错误日志没有被正确地输出或者存储
91
2
Windows环境下面启动jar包,输出的日志出现乱码的解决办法
146
3
Flink CDC产品常见问题之sql运行中查看日志任务失败如何解决
131
4
全新架构!日志服务 SLS 自研免登录方案发布
87524
5
Python使用多线程解析超大日志文件
90
6
Loguru:Python中强大的日志库
117
7
Python如何在打印日志时隐藏明文密码?
96
8
【二十九】springboot整合logback实现日志管理
147
9
Hudi Log日志文件格式分析(一)
90
10
Hudi Log日志文件写入分析(二)
22