There are two main evasion issues to be concerned with for any WAF - 1) Evasion of the engine/parsing itself These are usually impedance mispatches between the WAF and underlying app. There were some issues in the past with handling null bytes and multi-part filenames identified by Stefan Esser http://www.suspekt.org/downloads/RSS09-WebApplicationFirewallBypassesAndPHPExploits.pdf There was a similar recent one found by my SpiderLabs colleague Andrew Wilson where clients can specify random/invalid content-types and ModSecurity would not inspect it but the app would handle it normally. This was fixed in recent OWASP CRS updates. 2) Evasion of the rules There are always issues with negative security rules. You can test out evasions here - http://www.modsecurity.org/demo/crs-demo.html We had an SQL Injection Challenge last summer which included evasions for the ModSecurity OWASP CRS - http://blog.spiderlabs.com/2011/07/modsecurity-sql-injection-challenge-lessons-learned.html Hope this info helps.
mod_security
2012-02-16
1123
版权
版权声明:
本文内容由阿里云实名注册用户自发贡献,版权归原作者所有,阿里云开发者社区不拥有其著作权,亦不承担相应法律责任。具体规则请查看《
阿里云开发者社区用户服务协议》和
《阿里云开发者社区知识产权保护指引》。如果您发现本社区中有涉嫌抄袭的内容,填写
侵权投诉表单进行举报,一经查实,本社区将立刻删除涉嫌侵权内容。
简介:
There are two main evasion issues to be concerned with for any WAF -1) Evasion of the engine/...
目录
相关文章
ModuleNotFoundError: No module named ‘mmdet.version‘
ModuleNotFoundError: No module named ‘mmdet.version‘
1181
0
0
|
5月前
Py3 ModuleNotFoundError: No module named ‘Crypto‘;ModuleNotFoundError: No module named Cryptodome‘
Py3 ModuleNotFoundError: No module named ‘Crypto‘;ModuleNotFoundError: No module named Cryptodome‘
41
0
0
|
11月前
PYTHON3.x报错:MODULENOTFOUNDERROR:NO MODULE NAMED “CRYPTO“ 解决方案
PYTHON3.x报错:MODULENOTFOUNDERROR:NO MODULE NAMED “CRYPTO“ 解决方案
103
0
0
|
Python
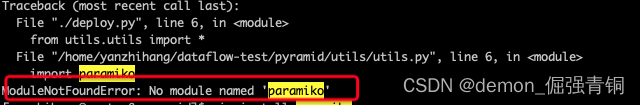
ModuleNotFoundError: No module named ‘paramiko‘ 和ModuleNotFoundError: No module named ‘scp‘解决办法
ModuleNotFoundError: No module named ‘paramiko‘ 和ModuleNotFoundError: No module named ‘scp‘解决办法
561
0
0
|
TensorFlow
算法框架/工具
Python
成功解决ModuleNotFoundError: No module named '_pywrap_tensorflow_internal'
成功解决ModuleNotFoundError: No module named '_pywrap_tensorflow_internal'
833
0
0
|
Python
|
Python
成功解决ModuleNotFoundError: No module named engine
成功解决ModuleNotFoundError: No module named engine
415
0
0
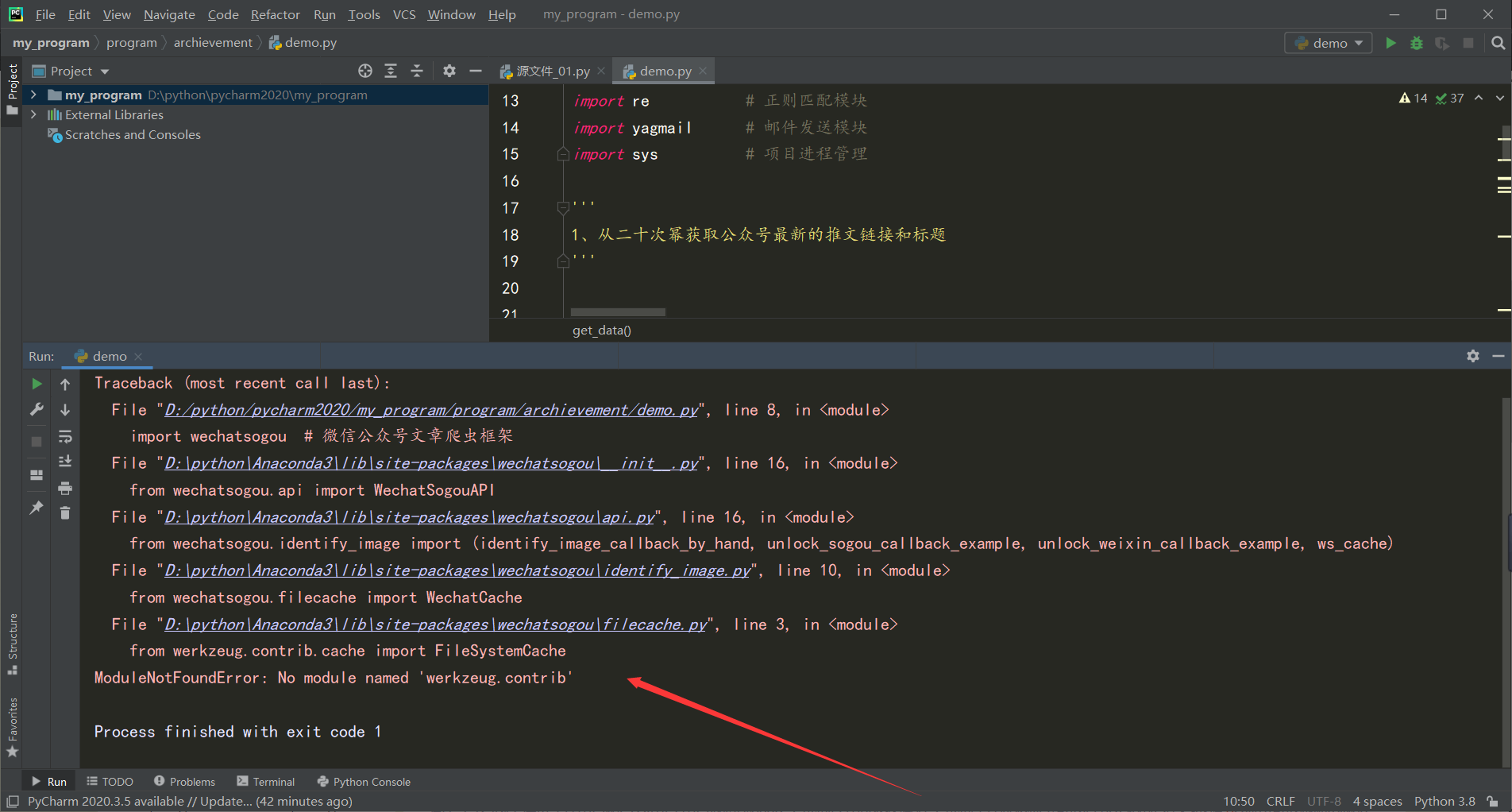
ModuleNotFoundError: No module named ‘werkzeug.contrib‘ 解决方法
No module named ‘werkzeug.contrib‘
933
0
0
|
C++
Python
import _polyiou ModuleNotFoundError: No module named ‘_polyiou‘
import _polyiou ModuleNotFoundError: No module named ‘_polyiou‘
410
0
0